Plesk comes with a bunch of apps preinstalled and ready to go. However, to customize the UI and configure the settings to exactly how you want them, it takes some time and know how. Luckily, we have a buzzing Facebook community who regularly share valuable insider info. Such as the top installations for a new Plesk server – which one member asked in one recent poll.
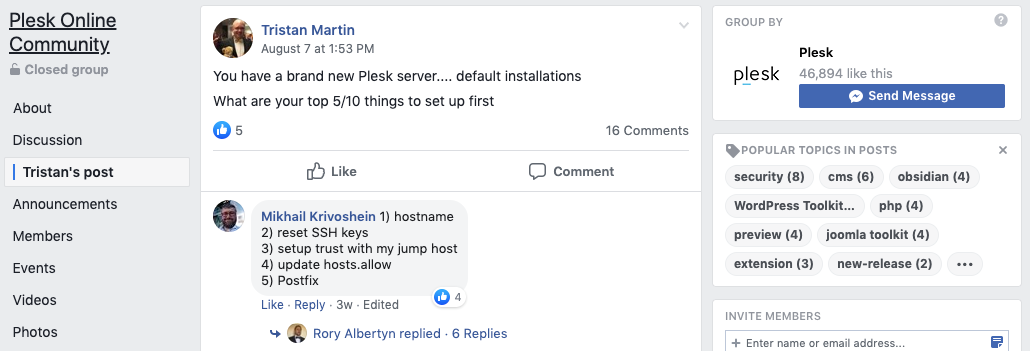
The Plesk online community is a great resource that can save new users tons of time and effort. There are nearly two thousand members offer each other advice, give and get feedback, and generally connect with other Plesk users. Safe to say, many of the members who’ve long been Plesk users had clear and practical thoughts on the matter.
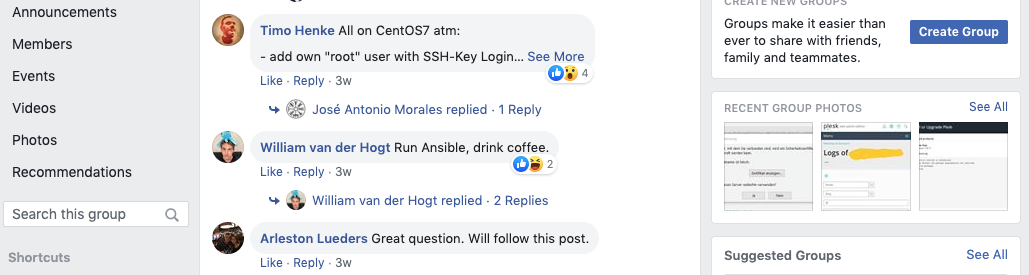
Some chimed in to support the original poster’s question. Whilst others offered answers that attempted to reduce the top five installations for a new Plesk server down to one. In this post, we’re going to round up some of most Liked answers of the poll. And so, without further ado, we’re presenting the top five things you should set up on a new Plesk server. According to your peers.
1) Configure the Server Hostname
As the label you will use to identify and distinguish your device (host) on a network, the hostname is undoubtedly one of the first things you should set up on your Plesk server.
You should make sure your server hostname is a fully qualified domain name (FQDN). A FQDN consists of two parts: the hostname and the domain name. For example, a mail server might be mymail.mywebsite.edu. Here, the hostname is mymail, and the host is located within the domain mywebsite.edu.
You specify your server’s host name during your very first login to Plesk. Specifying an invalid host name will result in unpredictable behavior. If this happens, or you need to change the hostname for any reason, don’t worry, you can do so once inside Plesk.
To change your server’s host name, follow these instructions:
- Log in to Server Administration Panel
- Go to Tools & Settings> Server Settings
- Enter the new host name in the Full Hostname As mentioned, this should be a fully qualified host name (FQDN), but without an ending dot (for example, host.example.com).
- Click
2) Reset SSH keys
Most Linux users will be used to connecting to their servers using SSH keys. SSH (Secure Shell) keys are access credentials used in the SSH protocol — a secure and widely used way to login from one system into another.
The strong encryption of the SSH protocol makes it ideal for remotely managing network infrastructure and issuing remote commands. But that’s not to say it’s bulletproof, and so resetting the SSH keys is another first step to setting up Plesk.
Since Plesk 12.0, you can use SSH Keys Manager to upload the public part of an SSH key pair to a Plesk server. Using this extension, you can easily manage SSH keys from the Plesk UI.
For every individual subscription, you can add or remove an SSH key which the subscription owner can then use to access the server.
To enable SSH access:
- Open a subscription
- Go to Web Hosting Access> Access to the server over SSH
- Select /bin/sh
- Click OK
To reset your SSH keys for Plesk on Linux:
- Connect to the server via SSH
- Create the RSA Key Pair
- The public key is now located in /root/.ssh/id_rsa.pub
- The private key (identification) is now located in /root/.ssh/id_rsa file
- Copy the public key to another server using the ssh-copy-id command: where user and IP address should be replaced with second server’s credentials
- Alternatively, copy the content of /root/.ssh/id_rsa.pubto /root/.ssh/authorized_keys on the second server
3) Manage Firewall Rules
The Plesk firewall configuration consists of two parameters: policies and rules. Policies are broad in scope and affect all connected to the server. Rules are narrower and govern incoming connections to individual Plesk services, such as SMTP or MySQL.
You can manipulate the policies and rules to either tighten up or relax your firewall’s security. For example, you can set a policy to deny access to all connections and set rules to allow a few IP addresses or ports. This will improve security but will mean some applications may not be able to work due to the network restrictions.
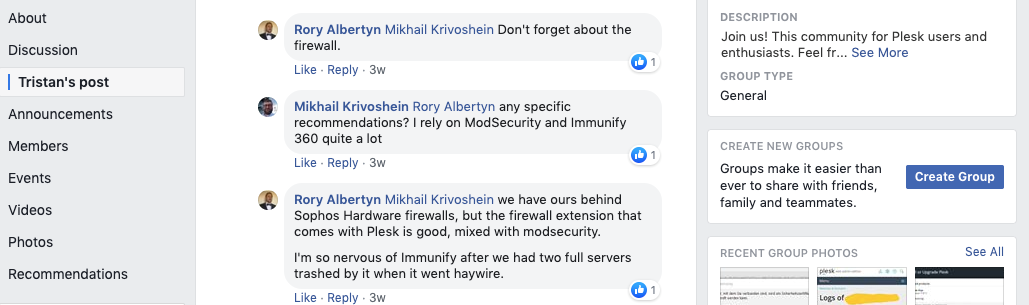
By enabling Plesk’s firewall, you’ll enable all predefined Plesk rules required for it to function. In Plesk for Windows, Plesk Firewall comes pre-installed. To install the firewall for Linux, you need to install the Plesk Firewall as an extension.
To manage and modify firewall rules via the Plesk interface:
- Go to Tools & Settings> Firewall
- Click Enable Firewall Rules Management
- Click Enable
- To enable/disable/modify firewall rules, click Modify Plesk Firewall Rules
4) Update hosts.allow
By default, remote access to Plesk databases is allowed from any computer. For security reasons, you may want to change this by allowing access from a specific IP address or prohibiting remote access altogether.
Linux has different types of parameters to restrict and control network access. TCP wrappers provide basic traffic filtering of incoming network traffic, relying on two configuration files as the basis for access control: /etc/hosts.allow and /etc/hosts.deny.
When a client attempts to connect to a network service remotely, these files are used to determine whether access is allowed or denied. You can therefore use /etc/hosts.allow and /etc/hosts.deny to define rules that selectively allow or deny clients access to server daemons on a local system.
The access control settings are specified individually for Plesk database users. Therefore, to make your settings work, the application must use the right database user’s credentials and access the database.
To allow client access, add the client host name or IP address in /etc/hosts.allow. Alternatively, to deny client access, add their name or IP address in /etc/hosts.deny. One thing to note is that access rules in hosts.allow apply first, and so they take precedence over rules specified in hosts.deny.
5) Setup Postfix
In setting up a mail service on Plesk, you have the choice of Postfix and Qmail. The question then is: which one should you use?
It depends on your needs. But Postfix is often ranked higher than Qmail as a Linux mail transfer agent. One of the main reasons for this is its modular framework, which means each module can be used, ignored, or switched with another depending on your needs.
You can check which mail transfer agent is currently enabled on the following page:
Server Administration Panel > Tools & Settings > Services Management
By default, Plesk for Linux uses the Postfix for sending and receiving mail through the SMTP and SMTPS protocols. You can switch to Qmail by running the following command:
# /usr/local/psa/admin/sbin/autoinstaller –select-release-current –install-component qmail
To switch to Postfix run the following command:
# /usr/local/psa/admin/sbin/autoinstaller –select-release-current –ins
There you have it: our top five installations for a new Plesk server. Of course, we couldn’t include all the Plesk community’s suggestions in this post, so leave a comment below if you feel we’ve overlooked any other important must-haves in order to set up a new Plesk server!

No comment yet, add your voice below!