DNS is applied when there is need to resolve any domain to a certain IP address. Linking a domain name to an IP of a server is called forward resolution and involves referring to DNS records called pointer records. These PTR records can also do the reverse: in other words, reverse lookup or reverse DNS lookup.
There is a specific PTR record, called the name portion, which stores entries that make reverse DNS lookup possible. The name portion is the IP address combined with “.in-addr.arpa”, this appended portion refers to the “address and routing parameter area”. Or, in other words, “arpa”. When using reverse DNS with IPv4 you make use of “in-addr.arpa” while reverse DNS with IPv6 uses “ip6.arpa”.
Reverse DNS: why would you use it?
You will use rDNS for exactly the same reason as the usual, forward DNS lookup. It is simply easier to remember a domain name rather than an IP address. That said, forward DNS is the important part of the DNS functionality: you can only find a website if forward lookup works. On the other hand, a website will load without problems even if there is no rDNS entry.
One common use case for reverse DNS is for email servers. Email servers can use reverse DNS lookup in the fight against unwanted mail. Some servers will automatically block any incoming mail from a sender IP address which does not have reverse DNS records in place. However, it is not a fool-proof method and is simply an additional trick email servers use. It’s a good idea to enable rDNS on your mail server, but it does not mean your messages will always get to an inbox.
Another noted use case for reverse DNS lookup is for server logs. It can render long logs in a more human-readable format by adding domain names, instead of just displaying IP addresses.
How does rDNS lookup work?
When you execute an rDNS request you query the DNS server of a domain to see if there is a pointer record. Without a pointer record the reverse DNS lookup will fail. If there is a pointer record the rDNS lookup will return a result. You can use a couple of tools which will execute a reverse DNS lookup command for you:
https://dnschecker.org/reverse-dns.php
https://mxtoolbox.com/ReverseLookup.aspx
Reverse DNS lookup commands can also be performed from the command line. In Linux, you need to run “dig” with an added flag, -x. Windows users can use nslookup. For Linux, your command, and the output, will look like this:
dig -x 9.9.9.9
with output:
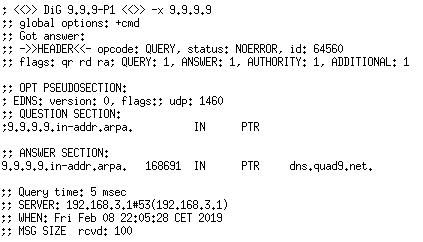
Look at the “answer” section: it includes the full reverse DNS pointer record for the IP “9.9.9.9”, and this leads you back to the Google subdomain “dns.quad9.net”

3 Comments
Reverse DNS is important. rDNS is not part of Plesk in 2020. Please add it.
Hey Tom,
Thanks for your feedback. Please keep in mind that reverse DNS is usually done on the side of hosting provider ( -> PTR record ), not hosting management software like Plesk or cPanel/WHM.
Hi,
Yes, but if you have your own IP address from RIPE for example, it’s important.