Security does matter! Protecting your sites from malicious attacks and preventing loss of sensitive data is a top priority for us. Plesk already provides a comprehensive set of standard security settings to start with but are you aware what the advanced security tools can do to further enhance security levels?
In this article, we will be focusing on a limited selection of security features and provide a brief overview. If you are interested in any additional security feature please leave a comment and we will get in touch with you.
Fail2Ban: Protect Your Server from Brute Force Attacks
Fail2Ban is an automated way to protect your server from brute force attacks. It monitors server log files for patterns corresponding to authentication failures, seeking for exploits, and other entries that can be considered suspicious. Such log entries are counted, and, when their number reaches some predefined value, Fail2Ban either sends a notification email or bans the attacker’s IP for a pre-defined length of time.
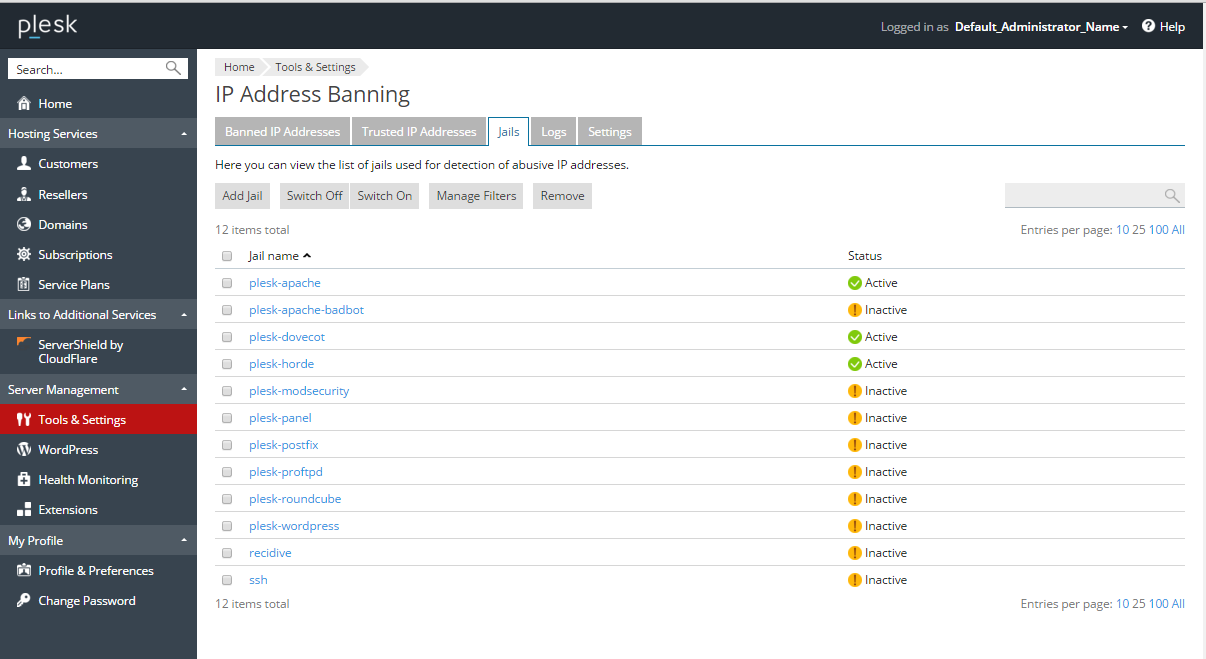
Fail2Ban should be installed as a Plesk component (see Plesk Components for the details). You can configure the Fail2Ban settings via the Plesk graphical user interface, at Tools & Settings >IP Address Banning.
Here, you can do the following:
- Create a filter that will be used to search the logs for suspicious activity. The filter is a set of one or more regular expressions.
- Create a jail, which is a set of rules covering an individual scenario. The settings of the jail determine what is to be done once an attack is detected according to a predefined filter.
- Activate or deactivate a jail.
- Specify trusted IP addresses, i.e., the IP addresses that will never be banned.
- Configure the settings of IP address banning, such as ban period, a time interval for detection of subsequent attacks, a number of failures before an IP address is banned.
- View the list of banned IP addresses and unban them if necessary.
Plesk already provides a number of pre-configured jails and filters for all hosting services (web server, mail server, FTP server). However, you can configure your own jail and filter according to your needs.
Find more details of configuring Fail2Ban in the Administrator’s Guide. The example of protecting WordPress installation with Fail2Ban can be found in the article Protecting Your WordPress Installations With Fail2ban.
Firewall: Control Network Connections
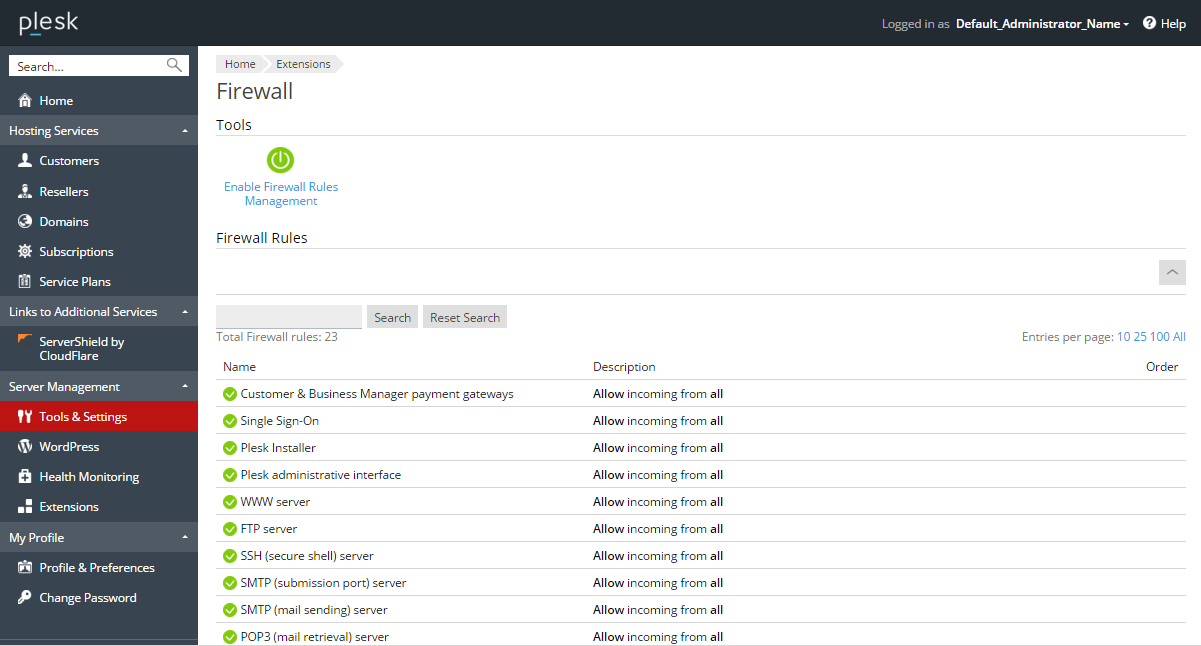
Plesk firewall allows you to protect a server from incoming network connections that could be used to compromise the server’s security. The firewall either allows or forbids connections to the services required for the proper functioning of a hosting server, such as web hosting, mail hosting, and FTP. The principle of the firewall functionality on Linux and on Windows is nearly the same; however, there are some differences.
For Linux, firewall is a Plesk extension. It includes a number of policies and rules. Policies are broad in scope and affect all connections to or from the server. Rules are more narrow in scope and govern incoming connections to individual Plesk services, such as SMTP or MySQL. You can use the mechanism of policies and rules to easily tighten or lower the security of the server. For example, you can use a policy to allow all connections to and from the server but use individual rules to forbid the connections from individual IP addresses – and the rules will override the policy. You can experiment to find the optimal trade-off between usability and security. For more information, refer to The Plesk Firewall (Linux).
For Windows, the firewall does not include policies. However, it comes with a set of predefined rules that allow connections to the services required for the proper functioning of a hosting server. You can add new rules, switch the rules on and off. You can additionally manage Internet Control Message Protocol (ICMP) communications that allow computers on a network to share error and status information and are used for troubleshooting purposes. For more information, refer to The Plesk Firewall (Windows).
You can manage the firewall in the Plesk interface, at Tools & Settings > Firewall.
ModSecurity: Prevent Web Applications from Attacks
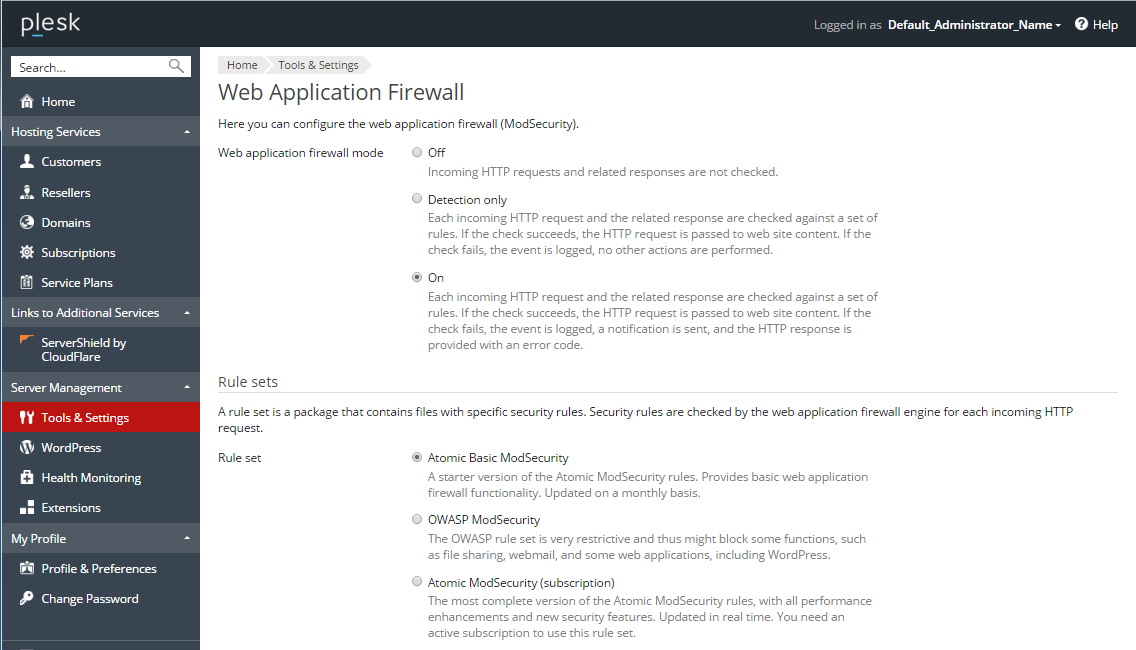
ModSecurity is a Web Applications firewall. It is a module of a web server (Apache on Linux or IIS on Windows) intended to protect your web applications from hackers and other malicious attacks.
ModSecurtiy checks each incoming HTTP request and the related response against a set of rules, and, if the check succeeds, passes HTTP request to the web site to retrieve the content. If the check fails, ModSecurity behaves depending on the selected mode: it either provides an HTTP response with an error code or just adds a corresponding records to the log.
There are several available rule sets, some of them are free, and some are commercial. The rules contain regular expressions that are used for HTTP requests filtering.
In Plesk, you can switch on ModSecurity, select its mode and a set of rules, configure its parameters, or even apply your custom, fine-tuned ModSecurity directives.
Find more information about ModeSecurity and available rules sets in the Administrator’s Guide.
PCI Compliance Resolver: Satisfy PCI DSS to Protect the Transactions
If you are using Plesk for processing credit card transactions online, by POS terminal or other methods, it is necessary to be compliant with PCI DSS – a constantly evolving security standard that helps organizations to proactively protect customer account data. As this standard has become widely recognized, non-compliance places your organization at risk of legal and/or civil consequences if credit card information get compromised. To learn more about the PCI DSS standard, visit www.pcisecuritystandards.org.
Plesk provides a special PCI Compliance Resolver utility that helps to make Plesk PCI compliant by applying a number of important security changes to web and e-mail services operated by Plesk (Apache server, Courtier IMAP, Dovecot, Postfix MTA, and so on). In particular, it allows to disable weak SSL/TLS ciphers and protocols.
The PCI Compliance Resolver works on Linux and is available from the Plesk installation directory.
Please find the detailed information about the utility usage in the Advanced Administration Guide.
What Else Can You Do for Security?
Besides the comprehensive security settings Plesk already provides today here are a few additional tips to enhance security:
• Get SSL certificates. In particular, you can create a free SSL certificate for your domain using Let’s Encrypt which is available as a free Plesk extension. For details, please refer to a separate article: Let’s Encrypt Plesk.
• Restrict access to Plesk from a specific IP addresses (learn more).
• Restrict connections via XML API (learn more).
• Protect databases by setting Enhanced security mode (learn more).
• Protect mail from spam by using the SpamAssassin filter (learn more).
In addition, apply some standard security recommendations that are still relevant for Plesk:
- Use strong passwords, as they are more resistant to various types of attacks.
- Change the standard SSH port (on Linux) or RDP port (on Windows) if there is a risk of a brute-force attack.
- Apply all necessary updates frequently and timely to enhance Plesk security and stability.









2 Comments
I’ve been using CSF LFD and Fail2Ban for a while and it’s been pretty prettyawesome! But Plesk should really include a lot more jails. Yeah you guys got apache,ssh,ftp, mail,wordpress, etc jails, but it would be awesome if you guys included other CMS platforms out of the box as well. Like Joomla, Drupal, oscommerce, etc. Right now I have to keep custom ones I find online and manually create custom filters inside Plesk Fail2Ban Interfance which is pretty neat! It’s easy to edit the jail file manually but the Plesk Fail2ban interface makes it so much easier. I just have to keep a backup of all custom jails. All in all A+
I can’t Find ModSecurity on my panel