Using passwords for authentication has its caveats. Strong passwords are hard to remember, while weak ones are easily guessed. Once you have to keep track of dozens of passwords, committing them all to memory becomes unfeasible; you start writing them down (images of a passwords written on post-it notes stuck to the monitor make security specialists wake up in cold sweat), or reusing the same password for different services (even if it is a good one, recycling a password is far from ideal). Using a special application like 1password is always an option, but some may baulk at the $50 it costs to use the version for Mac. All this makes one wonder: how do I reduce the number of passwords I need to remember without putting security in jeopardy?
Starting with version 12, Plesk comes with a number of features enabling you to log in to the panel without using passwords. Most of the authentication schemes described further are enabled by Plesk extensions. To install one of those, log in to Plesk, click Extensions in the left-hand menu, and then click Extensions Catalog. In this article I will be providing links to the Extensions Catalog website to make it easier to find the extensions I will be talking about.
LDAP Auth
I would like to begin with probably the least complicated authentication scheme extension on the menu today – one called LDAP Auth. It enables users to authenticate via LDAP. To make use of the extension the client must have been created in Plesk and must not be suspended.
Once the extension has been installed, open its settings and specify the hostname and the login prefix. The following screenshot illustrates the scenario with Active Directory integration.
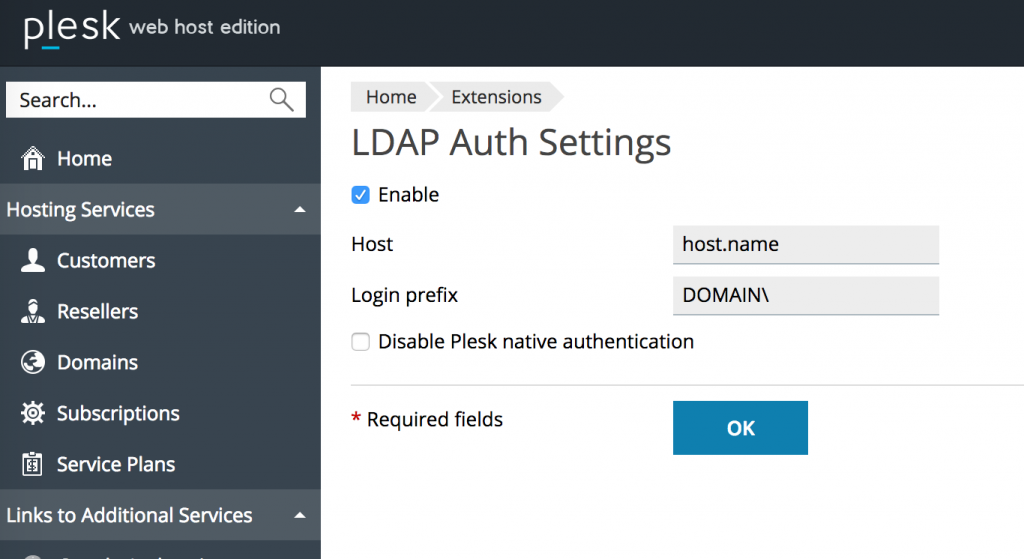
We are actively using this extension on Plesk boxes within the company.
Social Authorization
The next extension I’d like to talk about is called Social Auth. It enables authentication via various social networks. From the administrator’s standpoint configuring this extension takes some effort, but the end result is worth it.
For example, let us set up authentication scheme via the Google Account service. Note that we are not setting up integration with each and every individual service; we use the oneall.com aggregator instead. In most cases this lets us achieve the desired result much more quickly and easily. Register an oneall.com account, configure the required service (or services), and then enable authentication, specify the oneall keys, and choose the desired services in the extension settings in Plesk:
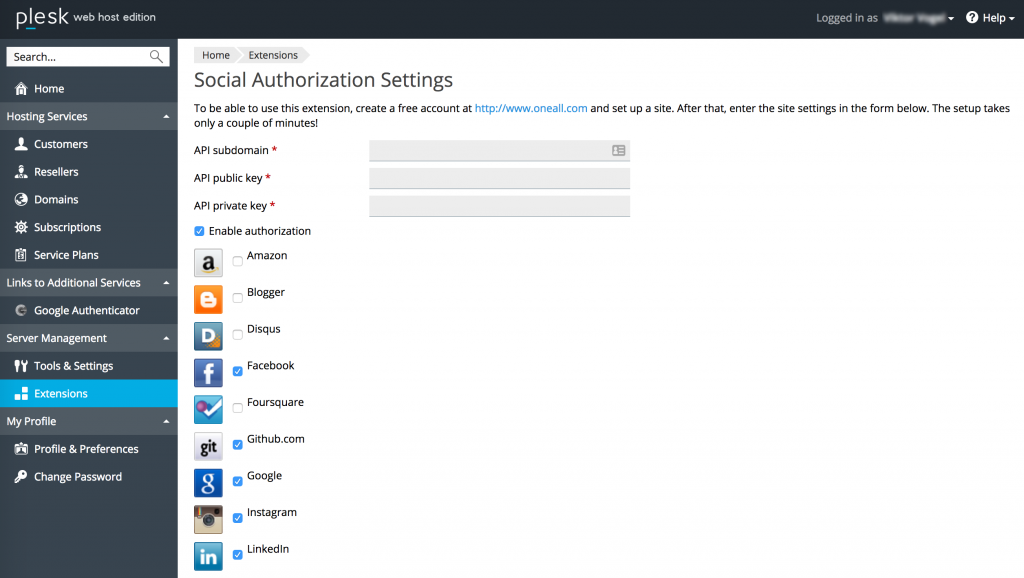 Once you have finished setting up the extension, extra buttons for logging in using the social networks will appear on the login page.
Once you have finished setting up the extension, extra buttons for logging in using the social networks will appear on the login page.
I am using this extension a lot on Plesk servers I administer that are located outside the company network.
Google Authenticator
Two-factor authentication scheme is facilitated by the Google Authenticator extension.
To make use of it you need to install the Google Authenticator application on your smartphone. Afterwards install the extension in Plesk and enable it. To configure the extension, first scan the QR code with your smartphone:
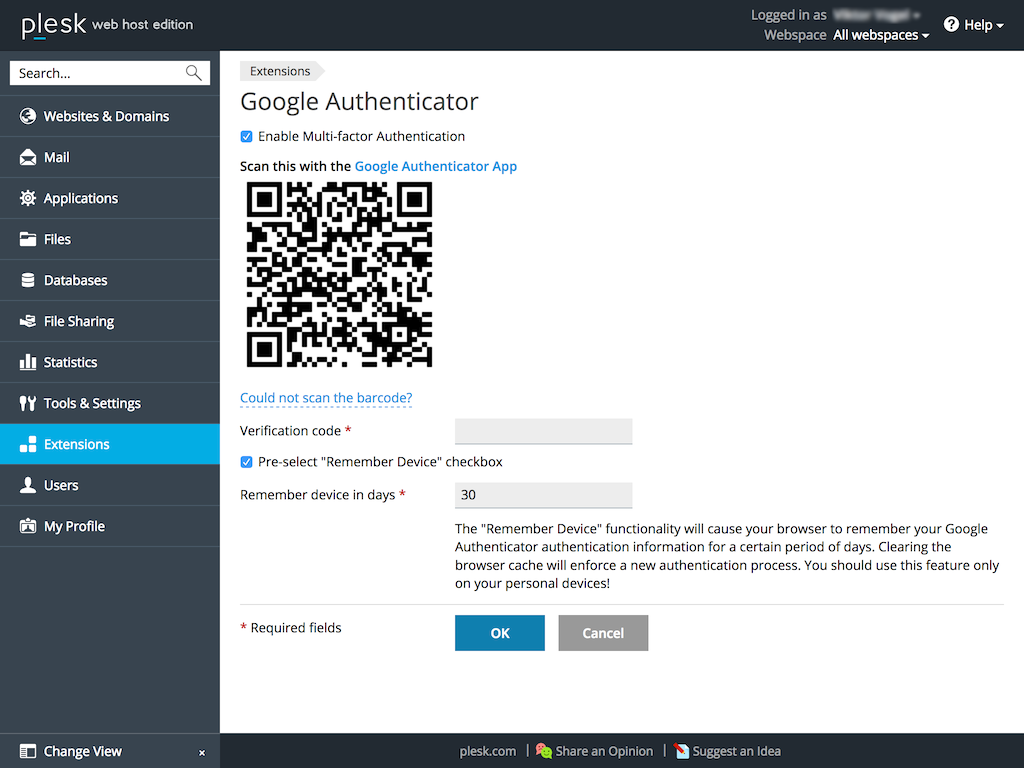
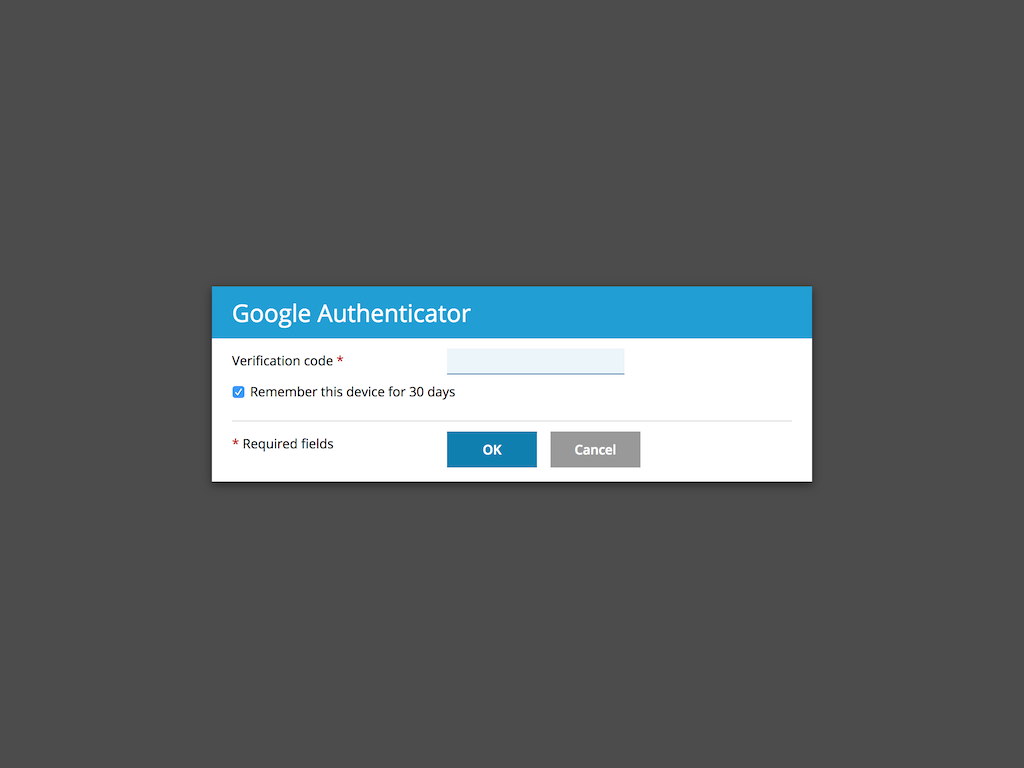
When you try logging into the panel, you will be prompted for a verification code. Refer to the Google Authenticator application you have installed on your phone to obtain the code.
Plesk Utility – login command
The plesk command line utility is used to wrap other Plesk command line utilities. With plesk login [USERNAME] a one-time login link for the specified user will be created. If no user is specified, the link for Plesk administrator is generated. The generated links can be used only once and become invalid after 24 hours since the generation time.
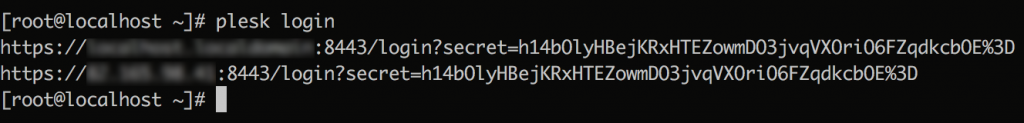
Read the documentation to learn more about Plesk Utitility.
Using Tokens
Using tokens is one more way of authenticating users in Plesk. We are not talking about any particular extension here; instead, we are talking about integration with other products and services. For example, say, you are a hosting provider, and you want your customers to have a “Log in to Plesk” button when they are logged in to their accounts.
Instead of simply posting a link to the Plesk login page, which would make it necessary for your customers to type in their login and password, you can set up automatic logging in to the panel (as we presume that the customer has already completed the authentication procedure to access their account).
“Under the hood” the mechanism looks like this: once the customer clicks the “Log in to Plesk” button, we send an API request to Plesk under administrator’s credentials to get the token, form an URL, and seamlessly insert it into to the customer’s browser.
You can read more about this functionality in the official documentation, found here: Automatic Logging In to Plesk.
SSH Keys
The last extension I would like to touch upon is called SSH Keys. So far we have been speaking mainly about authenticating users in the panel; however, the chief reason Plesk even exists in the first place is to enable users to manage their web hosting and the files in their webspace. To manage their web content, users can use the web interface, FTP, or SSH. Instead of making your customers remember their system users’ passwords you can set up the SSH Keys extension, add SSH keys, and have them used for authentication instead.
After the extension has been installed, browse to the subscription for which you want to enable SSH keys. Note the SSH Keys that has appeared on the Websites & Domains tab.
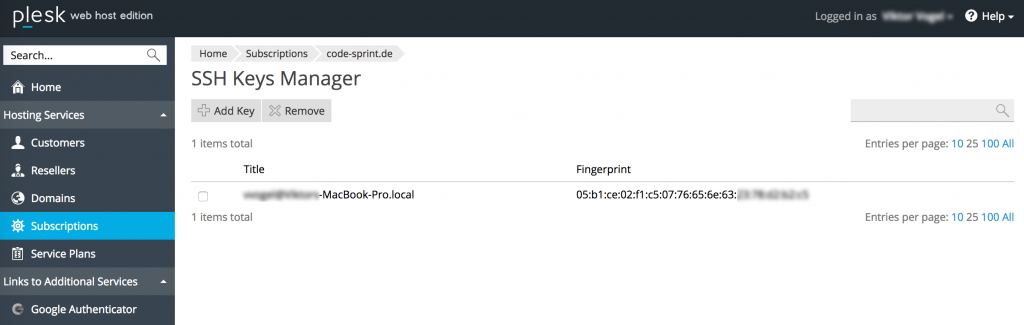
It contains the list of SSH keys that have already been created, and also allows you to add new ones.
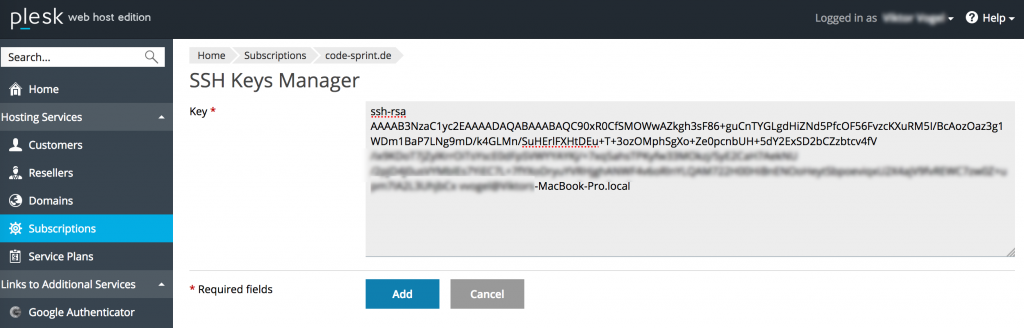
To enable the user to connect via SSH you need to turn on shell access for them. Browse Websites & Domains -> Web Hosting Access, select the desired option (for example, /bin/bash) from the corresponding menu, and click OK.
I am using this extension extensively (pun intended) on all my Plesk boxes, as remembering dozens of passwords for scores of system users is quite beyond my ability 🙂
Implementing your own authentication scheme
If for some reason none of the extensions I have been speaking about meet your requirements, you can implement one that is more to your liking. Refer to the Extensions SDK for information – I believe you will find API Authentication Hook to be particularly useful. You can use the source code of the LDAP Auth extension for reference – they are freely available.
In conclusion
If you are using Plesk and find authenticating using passwords tiresome, you have plenty of other options to choose from. Some may prove to be quite interesting, and suit your needs for everyday use.









25 Comments
Is there some more information on how to use the ldap authentication module?
I can’t get it to work.
LDAP extension is rather simple by itself (it performs “bind” procedure with login/password pair on selected server). But LDAP auth is very tricky to configure in some cases. You can try to configure some other LDAP client with your LDAP server. After success you can apply the knowledge to LDAP extension for Plesk.
Are there any changes that need to be made in /etc/ssh/sshd_config (or anywhere else) to use the SSH Keys Management extension?
By default there is no need to change anything in sshd_config. But you shouldn’t forget to enable shell access to particular system user (see the last screenshot).
Very interesting. When using Google Authenticator or Clef, what do you do if your mobile gets stolen or lost?
The only option is to login via SSH and re-install the extension or ask admin for assistance.
exactly why I am not a fan of google authenticator … phone screws up, phone is lost, phone is dead, phone is stolen
Comment reinstaller authenticator en SSH ?
Hi Pascal, please create a ticket so we can better support you! Thank you https://support.plesk.com/hc/en-us/requests/new
Hi there, if I understand correctly, this is a fine way to protect the web admin environment, but it is in no way a Plesk system-wide MFA and easily circumvented by not using the web interface.
For instance, using the iOS app, no Authenticator code is need to add the server and to view basic information (file access is restricted fortunately, and “Open in plesk” (not sure the English string) still opens the web version, requiring the Authenticator OTP).
Not yet familiar with the entire inner workings of Plesk, but it doesn’t seem like this is the proper way?
You can protect iOS app with secret code and TouchID (see “More” menu). Yes, right now there is no seamless integration between mobile app and MFA protected Plesk.
There is a problem with this plugin. Turned out, my Plesk Onyx and later updated to Obsidian got very slow on all plesk panel pages because of this plugin. It was worst on Domain Settings page – 11 seconds to render. I had to disable all modules to figure it out.
Of course this plugin was the last one, I would suspect. Switching it back again make the issue return.
Please, check the functionality of it.
Thanks for raising this Alex, we’ll look into it! In the meantime, if you keep having issues, best raise a ticket with support: https://support.plesk.com/hc/en-us
I use the google Authenticator, and it works great for the Admin Account. However, i cant find a way to Enable it for my users/customers, am I missing something?
hey Patrick – this article is a bit old. Can you perhaps contact our support with this? https://support.plesk.com/hc/en-us
Will this work with Authy?
Hey Mark! This article is a bit old, perhaps you can ask the support team behind it directly on here. And keep your eyes peeled for more updates on this topic – New info is coming soon. Thanks!
Yes it does
Hi,
I have a problem. I have installed the Google Authenticator for 2FA. But suddenly, the line is gone in my app. So I do not have the Plesk code anymore on my phone. So I am not able to log in to my server. What can I do to solve this problem?
Hi,
Although you should be able to use ssh to solve this issue, perhaps you can obtain some further assistance from the following article: https://support.plesk.com/hc/en-us/articles/213407229-Cannot-disable-Multi-Factor-Authentication-for-a-customer-in-Google-Authenticator-in-Plesk In case you need additional support, you can always reach out to https://support.plesk.com. Thank you.
Hi,
about Authentication for 2FA, its possible to enable this extension only for the admin user?
I want to have my admin user more secure, but our customers should still have access via user+pass.
So the extension is needed for every user after enabling?
Hi Marco,
We would kindly suggest you submit a request with our Plesk Support, as they can look at your specific case, and will be able to clarify this better for you.
Why doesn’t the Google Authenticator extension have the functionality to allow users to download backup codes?
Hi there, not sure, but are there even out-of-the-box “backup codes” for integrating 3rd party software with Google Authenticator? From our side, we did not try to simulate or implement this yet. However, you can always make a new request to share this interest with the community.
Also, the way to recover access is to uninstall the extension and install it again using CLI. It’s just an alternative to the “backup codes” (and it’s actually a bit more secure). Hope this helps.
Use LastPass Authenticator for MFA/2-FA, it saves your sites in the cloud where you can re-install and re-store everything on a new phone if needed.